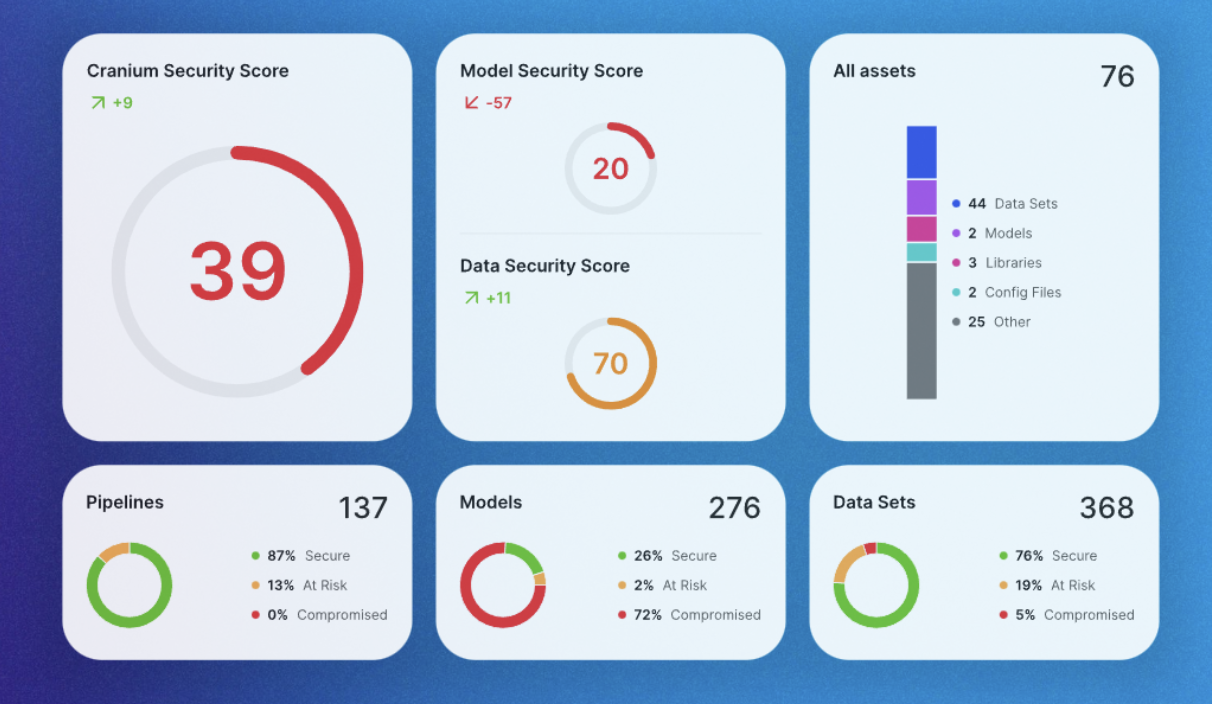
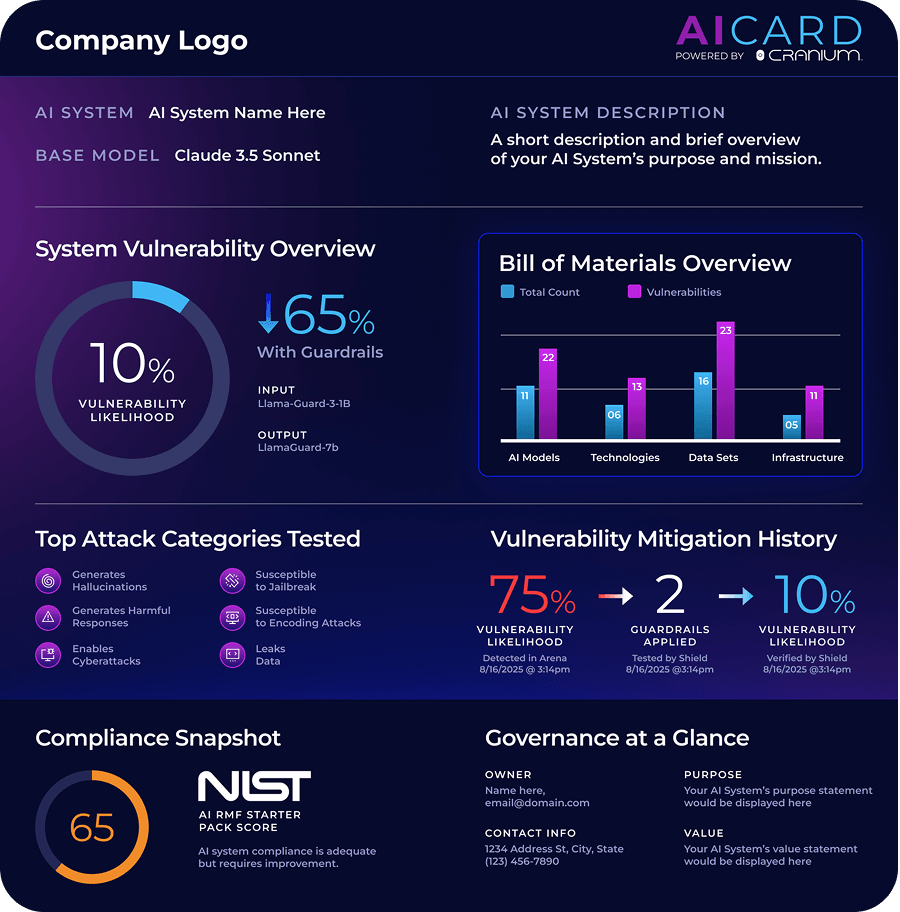
Limited Visibility
Shadow AI, embedded models, and unapproved integrations spread across code and cloud environments without formal review or security controls.
Unscannable Risk
Traditional cybersecurity tools cannot detect vulnerabilities within AI models or uncover issues such as model drift, poisoned data, or insecure APIs.
Expanding Threat Landscape
Attackers target AI-specific weaknesses such as prompt injection, jailbreaking, data leakage, and model inversion that legacy defenses cannot stop.
Lack of Continuous Assurance
Point-in-time testing cannot keep pace with retraining, new data sources, or dependencies introduced after deployment.