Chris Ward, Director of AI Red Teaming
Artificial Intelligence (AI) systems underpin a broad spectrum of applications, from autonomous vehicles to sophisticated cybersecurity defenses; the imperative for robust AI security frameworks has never been more critical. The AI Security Pyramid of Pain presents a groundbreaking approach, adapting the well-established Cybersecurity Pyramid of Pain to specifically address the nuanced and evolving threats targeting AI technologies. This whitepaper delves into the pyramid’s structured layers, offering organizations a strategic blueprint for enhancing AI security within the constraints of modern resource limitations.
The integration of AI technologies has transformed operational capabilities across industries, but this evolution comes with a new breed of vulnerabilities and threats. Traditional cybersecurity measures fall short in addressing these AI-specific challenges, necessitating a bespoke approach to AI security. Inspired by the foundational principles of cybersecurity frameworks and the pressing need for specialized security measures, the AI Security Pyramid of Pain emerges as a critical tool in the arsenal against AI-targeted threats.
THE AI SECURITY PYRAMID OF PAIN: A STRATEGIC FRAMEWORK
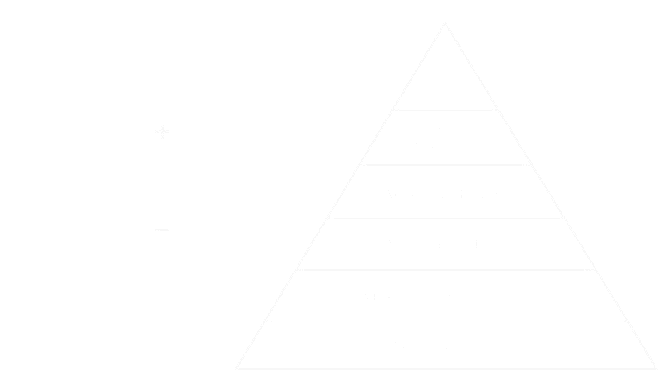
The AI Security Pyramid of Pain provides a strategic framework for managing the varied threats to AI security. As AI technologies develop, the associated threats will also change. Utilizing the pyramid model allows organizations to anticipate and respond to these threats, maintaining the integrity of AI systems. Future AI security will depend on ongoing adaptation, cooperation, and innovation, aspects that the AI Security Pyramid of Pain strongly endorses.
DATA INTEGRITY: THE FOUNDATION
At the pyramid’s base lies Data Integrity, emphasizing the importance of accurate, consistent, and secure data. This layer is pivotal, ensuring that AI systems function on reliable datasets, thus safeguarding the initial step in AI-driven decision-making processes.
AI SYSTEM PERFORMANCE: ENSURING RELIABILITY AND ROBUSTNESS
The next tier focuses on AI System Performance, highlighting the role of MLOps-driven metrics in monitoring and maintaining the health of AI systems. By prioritizing model accuracy, drift detection, and computational efficiency, organizations can preemptively identify and address potential security breaches.
ADVERSARIAL TOOLS: COUNTERACTING THE ARSENAL
The middle layer, Adversarial Tools, confronts the tools and techniques developed by adversaries to exploit AI systems. This involves a proactive stance in tracking, understanding, and neutralizing evolving tools that target specific AI vulnerabilities.
ADVERSARIAL INPUT DETECTION: SAFEGUARDING AGAINST DECEPTION
Advancing further, Adversarial Input Detection tackles the threats posed by manipulated inputs designed to deceive AI models. This critical layer employs anomaly detection, input validation, and adversarial pattern recognition to mitigate the impact of sophisticated attacks.
DATA PROVENANCE: AUTHENTICITY AND LINEAGE
Ensuring the authenticity and lineage of data and models, Data Provenance addresses the risk of compromised or biased datasets infiltrating AI systems. This layer underlines the significance of metadata tagging, blockchain for data tracking, and rigorous audit trails.
TTPS: THE APEX OF AI SECURITY
At the pyramid’s apex, Tactics, Techniques, and Procedures (TTPs) represent the most complex and challenging aspect of AI security. This layer demands a comprehensive understanding of advanced adversarial tactics and the strategic deployment of custom defense strategies.
The full manuscript (prepared for SPIE DCS 2024)…





